Okay, so I’ve had some friends and coworkers reach out over the last two weeks because they’ve been hacked through Facebook and, apparently, are selling items that don’t actually exist. Pretty sure its the same group doing the hack since the method is the same, but at the end of the day Meta simply does not care nor do they have any desire to get involved. Eventually, when a celebrity account gets hacked or enough users start bailing, Meta might sit up and start taking notice, but for now you’re on your own. So, this seems like a good time to refresh everyone on good internet safety practices.
Ultimately, you can’t focus on any one area of data privacy. We live in a connected world and it requires a blanket of protection. We are exposed to the elements. We will be in the elements. Our choice of blanket determines our protection.
Table of Contents
The Current FB Ploy
Let’s start off with the current game, and what prompted this lengthy post. What I’m seeing lately here requires an already hacked account or a account that impersonates a friend. It‘s pretty convincing, as it follows the established FB procedure for reclaiming an account.
In this case you receive a instant message from a friend on FB, or that friend’s impersonated account, telling you they were hacked or that they are trying to recover their account and that you will need to give them the code that is coming to your email so they can access their account. Problem is, this 2FA code is actually your 2FA recovery code and they have gone through the “Forgot password” route after obtaining your FB email from a friend’s profile or public records.
Once they have the 2FA code they change the account information including email, phone number, and any other common verification method (sometimes including the profile name) to lock down the account and prevent you from getting back in. At that point…its extremely difficult to unlock and obtain access to your own account.
The end goal, once account access is gained, is to sell items that don’t actually exist. In both cases I’ve ran across because the items were being sold from a person that was “known”, most people assumed that they were genuine and payed up. Unless your friends can convince the bank it was a fraudulent transaction, and in both cases the banks declined to refund because the transactions were initiated by the account holders, your friends are just out whatever they paid.
Common Sense Safety
Let’s go through some common sense safety steps; most of these are obvious, but again, both of the people I know thought they were participating in a “safe” transaction…and payed the price. So, let’s get started. We’ll break this down into several sections, starting with general best practices.
Best Practices
General best practices for online safety should be second-nature at this point. But, over 90% of people will still use a shared password to access important accounts. Even more, this “shared” password may have very slight differences, but it will still have the same base across these sites and programs with slight number or letter differences. Once the base password is compromised brute force will eventually figure the rest out. How many of you, when you have multiple passwords or need to change a password, have “passWord1, passWord2, passWord3, etc.”?
Passwords

Passwords are annoying. I get it. Its even more annoying to have 5,000 different passwords, so it’s just so much more convenient to have 1 password for everything, or 1 password but change it a little for different sites or accounts. That being said, people live for obtaining passwords (sometimes in bulk) and selling that information on the dark web; they may have no need for it, but someone else will always pay for that information.
Unfortunately, once that someone has paid for and obtained your password for a compromised account, they can, and often will, start using that password across other, more important accounts in the hopes of getting a match. While inefficient, it only needs to be successful a few times to pay off. So, while annoying, the easiest, and best, solution is to simply use a different password for each account.
Keeping up with passwords
I recommend using a password vault with a password generator. If you want to go really old-school you can keep everything written down, but that becomes a pain when you get more than a handful of passwords and you have to change those passwords.
There are a ton of different options for vaults; you do not have to pay for a password vault. Don’t fall for fancy options that promise a ton of features for a price. My go-to apps are:
Microsoft Authenticator
Google Authenticator
Authy
C2 Password
Most of these also include 2FA options and can sync across your devices. MS Authenticator, for example, rolls 2FA and passwords into one app on your phone that will sync across your phone and desktop/laptops and tablets via a browser plugin for MS Edge. C2 Password from Synology works similarly, but 2FA is a little more complicated to setup but it has a little more robust web interface. In any case, let the vault do the hard work of setting up a complex password for each site.
Something else each of these apps will do is monitor your passwords and compromised sites to let you know if you have had a breach that exposed that password or if you have a shared password. You be walked through changing those passwords, and in some cases that app will even sync directly with the site to update the password in one step.
2 Factor Authentication
2 Factor Authentication (2FA) is also annoying. Just like keeping up with passwords 2FA is yet another step to getting into an account. With the prevalence of mobile devices 2FA is unavoidable in most places. That being said if you can set up 2FA for an account, do it. It’s yet another layer of protection around your account. Likewise, once a device is trusted it won’t require 2FA again unless you clear the browser cookies or the authorization times out.
2FA exists in several flavors, including one-time passwords (OTPs), time-based one-time passwords (TOTPs) push authorizations (notifications sent to your mobile device(s) that require a physical response), email link authorizations, SMS authorizations, and even phone OTPs. Push authorizations sent to your mobile device(s) and TOTPs are some of the most secure methods, as they require you to login to your mobile device and physically approve the login or type in the TOTP from your authenticator app.
2FA apps, like password vaults, are free. MS Authenticator, Google Authenticator, Authy, and Synology Secure Sign-in are all examples of 2FA apps. Setting up 2FA is specific to that site, but in most cases is straight-forward and involves adding a login and scanning the QR code (generated by the site you are setting up 2FA for) to add the secret key that defines the time counter.
Social Media

Unsurprisingly, social media is the easiest target for hacks, scams, and cyberstalking/bullying. Hacks commonly originate from other hacked profiles or impersonated profiles. It takes 5 minutes or less for me to make a profile that would look like anyone I wanted it to look like. With AI and post generation the profile I make will look real enough to convince 60-70% of my friends that it’s legit.
All those friends...
It can be said that a measure of a person is to see how many friends he has. Or something like that. That being said…how many people do you know that add friends that they may not have even really met? Or see personal accounts with thousands of followers? While the beauty of the connected world is that we are just that…always connected, it also invites problems. Case in point, many hacked accounts are hacked because a friends account was also hacked and the user is responding to a new “friend” invite. Your exposure and risk increases with your number of friends; my risk of exposure with 87 friends is significantly lower than the risk of exposure of a person with 2,000+ friends. So, should you necessarily friend the random person you met in the Uber last weekend and talked to for all of 5 minutes? Probably not. Probably also shouldn’t add the person that added you because you were a friend of a friend (we’ve all met those…). Cleanout time.
Buying and Selling
Another popular trend I’m seeing is the “closet cleanout” trend. Rather than going through an online marketplace it is simpler to post all the items being sold in a timeline post or story and let the free-for-all commence in the comments. While that may be a great way to do a closet clean-out and an easy way to remove items, it has also opened the door for the type of scams I’ve seen over the last few weeks.
Here’s the problem: selling through a simple timeline post has ZERO buyer protections. Let’s put that another way:
If you plunk down $1,000 on a hot tub in a timeline post and then pay that person through Venmo or Paypal (or your platform of choice) and then find out it was not real...you're just out that $1,000 dollars with ZERO course of action.
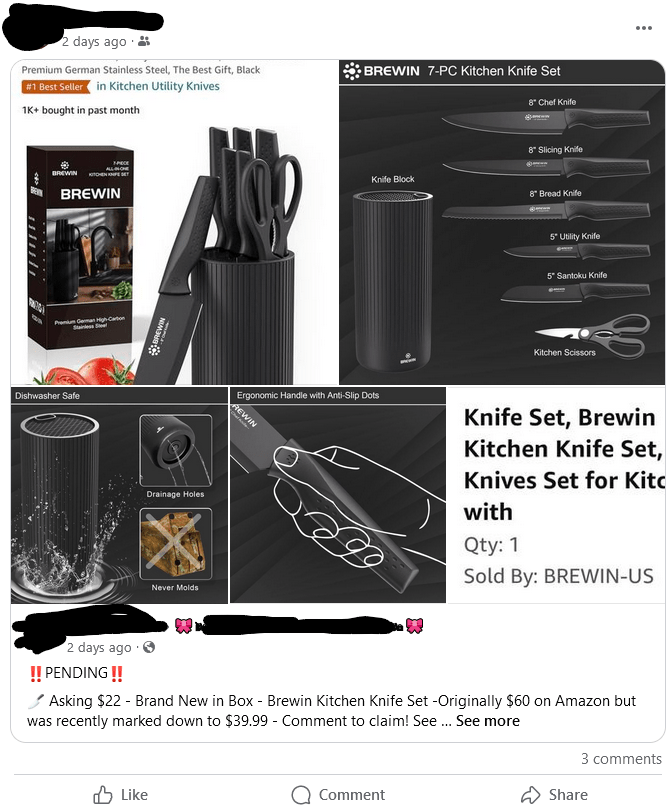
One of the posts above is from a hacked profile. The other is from a legit seller. Do you know which one is which? The left picture is legit…the right…not so much. Same profile…but the post on the right was put up by the hacker. Since this person only sells through posts and not a marketplace or ecommerce site, it was easy to replicate previous posts and ask buyers to simply send payment to a Venmo account that looked close to the actual seller’s account.
Be safe as the buyer
Only buy from people you know
If it seems too good to be true…it probably is
Don’t assume that because you know the person it is safe
Never pay up front…and if that means shipping an item…stay away from the social media sellers and buy from a geniune Ecommerce site (Ebay, Etsy, etc.)
If the buyer is a close friend…text them through SMS or better yet call them to verify a purchase first with the number you know is legit. Don’t message through the social media app.
Do your research on in-app ads. Clicking through an ad link may not always take you to the intended destination. Check the company by first manually going to the site in a browser before clicking through, and make sure the link you followed is correct (i.e., are their misspellings or changes to the domain name versus what can be visited in the browser?)
Realize that buying through Ebay, Etsy, or verified sellers typically will come with some buyer protections against fraud. PayPal may also have some built-in protections depending on the seller, since as a payment platform it is in their best interest to keep fraud to a minimum to prevent a mass exodus and a reduction in transaction fees and thus revenue.
Be safe as a seller
As a seller you should present yourself as a legitimate, serious source of a product. Buyers should have as much information as possible, but just like a buyer selling has risks involved as well.
Sell through a recognized platform (FB Marketplace, Etsy, Shopify, etc. depending on your need).
Don’t ever give “potential” buyers personal information; as an example I had a suspected takeover attempt last week on a product I was selling through the marketplace. The “buyer” said they would prefer to email me and would like to continue discussions through my personal email. When that didn’t work, they asked if I would be more comfortable discussing the sale through text on my personal cell. Both are recognized attempts to gain account access through personal identifiers. When I responded that all buying/selling conversation would be through the app, the “buyer” disappeared.
Provide as many details as possible about the item being sold. Fraudulent postings often only have 1 or 2 photos of the item and are lacking in significant detail.
Selling in volume? It really doesn’t take much to set up a Shopify site or even host a site with WordPress and WooCommerce. You’re not responsible for payments other than to setup the links through your payment vendor.
Rules for BOTH
Regardless of your position as the buyer or the seller, the following are good practices in either case:
Use verified payment platforms for transactions; never use a personal check or accept a personal check unless it is someone you know personally and the transaction is in-person. Yes, you will have a transaction fee as a seller. My own, very personal opinion, is that the transaction fee is worth the risk mitigation. Don’t like it? Do personal family and friends transactions through Venmo or PayPal or add in the transaction fee to the price, but I would only do those personal transactions with actual friends and family.
For local pickups or drop offs, pick a neutral, public location if possible. Many law enforcement offices have monitored meet up locations now. Not gonna lie, I’m usually packing for the handful of times I’ve done this.
Private Message Links
Links in DMs or Private Messages (PMs) are fun. On the one hand…they sometimes are from real people you know and trust. On the other hand…your friend’s profile may have been hacked and the link you get may send you to a compromised site that loads a malicious piece of code.
At the end of the day, the best advice here is to trust your gut. At the very least, you can text or message someone back if you get a strange, or random, link and simply ask if it was legit. Otherwise…don’t follow it especially if you are not expecting it.
It should also go without saying…never respond to a friend with a 2FA code or personal information unless you are expecting the request (although…even if you are expecting the request…just NO to any 2FA codes).
Cyberstalking or bullying

Cyberstalking is a discussion that should take place as soon as a child has access to a computer, in my own opinion. Especially if that child, as is commonly the case today, has access to games that allow instant messages or chats.
Until they are out of the house and well on their way to college, most children’s brains simply don’t have the development to effectively process and handle the increasingly convincing and constantly changing methods cyber criminals utilize to influence children.
I’m mentioning this in the Social Media section because, while FB and Instagram are losing market share to other, newer platforms like Snapchat and TikTok for children, teens, and young adults, it is all lumped together and adults (especially some older adults) fall victim to these as well because they forget basic, common-sense rules. Just like I was taught when the internet was mostly dial-up and Yahoo! was the big search engine of choice, you don’t talk to strangers. You certainly don’t engage in personal discussions with strangers (in-person or online). Would you give your phone number to a person on the street that you had never met before? Why would you do it online? Your best friends, and family, will always be able to get in touch without the need to go through social media if its a matter of money.
Email Safety

Do you work for a corporation? If so, how often do you get test phishing emails? I get one at least once every couple of weeks just to make sure we stay on our toes. That being said I do miss when email and malicious website code were the main online dangers.
Just like social media, email safety involves using your head and common sense. It can’t be said enough:
Don't click a link unless it is expected and you are familiar with the sender. If in doubt...ignore it.
Unfortunately, you have to be extremely careful. We live in a connected world were power comes from information. Specifically, your information. What you do. What sites you look at. Where you go. Most of this is based off of information your mobile device collects, but anything you do online is tracked by someone or something and stored away. Large companies like Google, Amazon, and Meta are sources of vast amounts of information about users’ browsing habits and interests, and advertisers happily pay them for that info. Since our Alexa devices and mobile devices are always listening…how else do you think the ads for that “fill in the blank” item start showing up after the dinner discussion?
Now, with regards to email, that same info is available on the dark web sometimes. So, to use an example from a few years ago when we tried to set up a retreat with the cousins, I received an email from a cousin that had a PDF attachment. This email met the following benchmarks for legitimacy:
It originated from a family member, and the “from” was a known email address
It had the correct signature for this family member’s email
The subject and content referenced the recent discussion about renting a cabin for a cousin’s retreat
The PDF was supposedly a quote for the week and just needed “approval”
The only way I would’ve known this was a phishing attempt was by reaching out and asking if it had been sent; not by email but by text, and by digging into the send history. It varies by provider, but if you click on the options for a specific email and hit “Show original” it will bring up a big page filled with HTML and email code. Digging into the original email I could see that, while the “from” address was actually an address I knew, the email actually originated from another email address. In other words, this attempt was pretty damn good and relied on both information that was being mined from a current discussion thread and a possibly compromised account.
So, what are good practices?
Don’t click on links unless you are expecting them and if something seems off, verify it. Remember, most legitimate web sites do not send emails asking for information or have you verify with a link without you first requesting it and generally it will expire quickly (the email will tell you as much usually)
Check your “from” address and make sure it is known and double-check spelling and format
Check the email content; does it make grammatical sense and is formatted correctly?
Links should also make sense; for example a link from Amazon should actually be amazon.com, not amaz0n.com, amazon.us, or something similar.
If in doubt, delete it. If it’s important, it can be repeated or resent.
Internet Safety
Remember what I said earlier about your information being valuable? Somebody is always willing to pay for your information. There is a common phrase in IT…Zero Trust. In other words…trust nothing.
I’m very privacy-centric with my data. If I don’t need to share it, I most likely won’t. I have a handful of sites I visit often, and for the most part don’t really participate in social media. I may browse, but very rarely do I interact. I have my own cloud storage rather than rely on a larger third-party storage center. That being said, I also realize it’s a lost cause to expect complete privacy in a connected world. But…you can be smart about what data you share, where you share it, when you share it, and who you share it with.
Being smart with your data
Data privacy starts with one question: “do I need to share _____?”. Further, “is it absolutely necessary that I share _____?”. Because once it is shared, its like Pandora’s box, it can’t be undone and it is out in the digital world for everybody to see.
The next question to ask, once you’ve determined its necessary, is to ask “is this limited in scope?”. Or, to put it another way, if we toss a stone in a pond how big are the ripples going to be? Is it a big stone? Or a small stone? Smaller the stone, smaller the ripples. Smaller risk, smaller impact. Use, as an example, your physical address. If a malicious actor breached a site and obtained your personal address, how big of an impact would this be? Since your personal address is a public record, most likely it is a small impact. Now, how about banking information? Big impact. But…we offset this risk by limiting where this information is used and stored.
Another question to ask is “does it make sense?”. This is a little broad, but in a nutshell, does the data requested make sense for the site you are using? For example, the fitness site we have set up for Brittany asks a ton of questions in the client questionairres. But, we only ask broad questions. We don’t ask specifics, unless it’s relevant to that particular program. As a more specific example, in the nutrition program we ask specific information about dietary habits, location, and family habits. We explain why we are asking as well; i.e., we find families with children often look for quick-service meals more often, and people in rural areas often struggle to find some ingredients at grocery stores that people in urban areas can find anywhere. If you’re buying a dog collar off of a pet oriented site, those questions would have no business there.
Limiting your data
So you’ve shared your data; it’s out there. If you’ve walked into a big box retailer, even if you have ZERO web presence, you have shared some data (look at Rite Aid’s lawsuit over facial recognition in stores). That’s a low risk share and you can’t control it. But, control what you can control.
Banking and Payment
Let’s start with banking and payment. How many sites have your credit card information stored? You hopefully can count that on 1 hand. While it’s convenient for Papa John’s, Pizza Hut, Amazon, Wal-mart, Ebay, PayPal, Ridge, Google, and who knows who else to store your info, it increases your risk. If any 1 site is breached that saves payment information and an actor obtains payment info, you’re SOL. Limit that payment info to as few places as possible, and never save your card information in the browser. For example, I use PayPal for almost all transactions. One, if my card changes I only have one place I need to worry about. Two, PayPal, while it is a big target for hackers, also invests heavily in security and encryption. Three, PayPal has policies and procedures that protect buyers and sellers against fraud. I’m not promoting PayPal, but it’s been around the longest. Choose your provider and stick with it.
Location, location, location
Another big one…location. Simple answer…unless it’s absolutely required, don’t. Yes, it makes typing in addresses easier (since they’ll autofill), and yes, it can provide all kinds of fun places to eat, shop, and visit. But…especially on public WiFi it can be problematic. So, the best answer here is unless it’s a requirement, don’t. That includes phone apps.

Say Cheese!

Actually this is a hoax. None of the social media platforms “own” your photos or media. But, I thought I would address it here…you have sole control over your content. You don’t have to post the whole “I do not allow…” or whatever.
That being said…you DO allow the platform rights to republish media, censor it, edit it, or remove it. Likewise, be careful about WHO or WHAT is in your media. In general, you should ask permission if other people are in your photos that get posted, especially if they are children.
The other point I’ll make here is that online predators will often start with family photos and work from there. This is where the “blanket” comes in that I’m going to get into in a little bit. You should have provided your children, and family, with a blanket of protection so that they feel comfortable coming to you if something out of the ordinary occurs. Control what you can control. It goes back to the first part of this section…what you share, where you share it, when you share it, and who you share it with.
Watch your links
Be careful on your clicks! Search engines and ISPs are okay at filtering malicious links, but it’s a race between the security companies and the scams. In general, don’t put your information out on a site that your gut tells you is wrong. In pharmacy we live by the saying “if your gut says it’s wrong, it’s probably wrong”. The same goes for the web. If you’re on a site that is loaded with ads or starts throwing in a bunch of pop-ups, or doesn’t offer payment through a verified vendor, be cautious. Do your research.
As an example, for piano tuning I have a site set up to make appointments, pay an invoice, or pay directly. I have no pop-ups, do not advertise on the site, and payment is through Stripe or PayPal only. If I send an invoice, I do it standing in front of you and the payment is through PayPal or Stripe; I do not store payment info. If the site seems sketch…it’s probably sketch.
Another fun trick is advertisements in the browser. Some of these ads are actually embedded code that installs a tracking cookie or program on the device. In many cases the code is benign and collects specific information (although…still not good). But, in other cases that code can be more harmful and actively send information back to a dedicated server. This can be location, contacts, keystrokes, or anything else the browser has access to.
The Blanket

Mmmmkay. So this all leads up to the point of this long thing. You can’t take one piece and only one piece. Everything layers together. The thicker your blanket, the better your protection.
Look at information security as a multi-layer approach. It’s cold out. First up, you’re going to stay in inside, walled off from the cold inside a nice, warm, home (more on that in a minute).
Second, you’re dressed in something cozy and warm, probably with the fireplace heating things up nicely.
And last, a good wool blanket finishes it off (maybe with a coffee splashed with some Bailey’s too…).
All in all, you’re cozy. The cold is kept at bay by good walls, you’ve got some passive coverings to stay warm, and an active fire working to keep the last vestiges of winter away. I say this as it’s 92 degrees outside. Some irony there with this analogy. But anyway…
The First Barrier
How about that firewall. Think of the walls of the home as a physical firewall. Most devices have a firewall; computers, routers, phones, etc. These are the digital barriers that prevent brute force attacks on your personal information. Don’t bypass them. In most cases they act independently with no intervention required on your part. Hooray for that.
If you really want to get fancy and add another layer of insulation…get or program an ad blocker. Some routers have these pre-installed now, or you can very easily and cheaply make one with a Raspberry Pi or always-on computer. Watch how many web sites start asking you to turn it off so they can make money on their ads.
That first layer
Now we’re moving on to the choice of appropriate clothing. Or, in other words, your digital behavior. Be SMART.
Use a password vault and generate unique, strong passwords for each account
Be skeptical of all incoming traffic. Question everything.
Think about necessity…is it really necessary to share it. Is it duplicated somewhere else?
Trust your gut. If it seems sketchy…it probably is.
Do your research. See an ad on social media…verify it independently through a browser. Use the hive…reviews are often make or break for legitimate sites. If you see all 5 star reviews, or all negative…be cautious.
Should I really click that link? Did I generate a request that sent that link?
I have 5,000 friends. Maybe I should clean that up…
Where is my payment information stored…?
Stoke that fire
Believe it or not malware, adware, and viruses are still a thing. Trojans too. You should have an active agent passively scanning your network for unusual activity. Whether its Microsoft Defender or some other software, you should have something internally keeping malicious code and software at bay. In my case, my router actively scans my network for issues and unusual activity. Likewise, besides blocking ads AdGuard Home blocks known malicious IP addresses.
Nothing like wool...
I’ve got a big ole’ wool blanket on the bed for winter. Nothing like it. Think of it like 2FA. Or an overly paranoid dad with a tech thing. That blanket is there to act as another layer of defense. It’s like requiring two people to launch a nuclear warhead. Most malicious actors will go for low hanging fruit and move on. While they are getting more skilled and adept at avoiding 2FA (see the current FB scam), 2FA still thwarts most of them if you use common sense. The common denominator is that it requires your permission at some point.
Never. Repeat: Never. Ever give a code to even a friend. Period. End of discussion.
That 2FA is that final layer of defense; somebody tries to get control…and you have to physically approve it. Unless you have initiated it first, there are absolutely ZERO reasons to confirm a code with any request through messaging. Any 2FA code requests will ALWAYS be entered directly on the site.
Once you send that code…it’s game over and you’ve now got a whole bunch of work. Potentially lawsuits. And identity theft. Just. Don’t. Do. It.
The VPN

Let’s talk about if you’re outside your home network and your basic layers of protection. In general, mobile networks are okay. There’s a lot of people on a single tower at once, so you’re a minnow in a school of minnows. Plus, mobile networks require a little more authentication and typically are not easy targets.
Public WiFi hotspots, on the other hand (especially airports) that are unsecured…different story. These are prime for Man-in-the-middle attacks. In other words, somebody techy is sitting on the same unsecured network siphoning info off of anybody else on that network. That’s where a VPN, or Virtual Private Network, comes in.
The beauty of a VPN is that it encrypts your data between you and the server. In a public WiFi no data is encrypted and is open to anybody with the tools to see devices and traffic on the network. If a user has a VPN enabled on that network, however, data on the device is encrypted between the device and the VPN server. In other words, that device is connected to the public WiFi server, but appears at the VPN server and all data is encrypted between the device and the VPN server.
Many routers now have a VPN server built in. You just have to enable it and set it up. Some of the more common VPNs are WireGuard and OpenVPN. Do not pay for a VPN. Paid VPNs will most likely sell your information. If you travel or connect to public WiFi often, it is worth it to either check your router for a VPN, or set up your own VPN server with a Pi or always-on computer.
For the parents...
An extra layer here now that I’ve got to stay on my toes…but how to make sure the kids are safe. My kids have experience only with Mine Craft. Nothing else. And that Mine Craft is actually a private server I monitor pretty close. I recently listened to a lecture from the state police on online crime. It was not surprising, as I stay pretty aware of the current trends, but just reaffirmed the steps I take and the services my router and ad blocker hide.
Many of the trendy apps today are also top hangouts for child predators. Snapchat in particular is a troublesome app, especially for law enforcement because of the nature of the messages on that platform. Apps like FB, TikTok, and even Reddit are usually stepping stone apps to Snapchat, as predators will try to lure children to Snapchat from other apps that have persistent messages. Additionally, the controlling parties that own these apps are less than cooperative with law enforcement in the course of an investigation, so in the event of an actual crime the course of action is often limited, and according to a law enforcement officer I talked with if the guilty party is in a foreign country the crime will often go unpunished even if the app owners cooperate.
Proactively block anything you have issues with or just don’t recognize. Most routers, especially those with Xfinity, can block ads and services. If you’re not sure, ask me. I’ll help you figure it out. I actively block almost all apps and services that are not necessary for network functionality and have any device the kids use on a separate network that has strict permissions and time limits. There are also several apps out there that help monitor and control screen time and activity; that being said, the best results start at the home with set limits and respect. Tech only goes so far, faith, values, and family fill out the rest.
Securing the phone
One of the most controversial topics of discussion is “when do I get a phone?”. Up until recently, in our house it was “when you’re old enough to drive”. Unfortunately, between Boy Scouts and ballet, we found ourselves in a scenario where our daughter was out of ballet early and didn’t have a way to communicate with us. So…that started the process. So…let’s look at how we can lock down that phone.
Parental Control Apps
Parental control apps help keep your kid safe by allowing you to restrict, control, and in some cases monitor, all activity your child is doing on their devices. The best apps, in my opinion, are those that offer control across multiple devices. To that end I tend to stick with Google and Android products as they tend to be consistent across multiple devices, whether its a Chromebook, phone, tablet, or Fire device (yep…you can use Google Family Safety on Fire tablets if you really need to do it). The big downside, as I have found out over the last few days, is that natively Google does not support any app that specifically monitors and logs calls and texts. While I disagree with this approach, I’ve found that I still have a high level of control over the apps my child has access to, and there are ways around it too.
First up, though, lets look at some of the options out there. For a complete run-down of each app, I glanced at an article in Tom’s Guide. As a tech resource I’ve found this website to be pretty spot-on with its information, but others like PC Mag, TechRadar, or SafeWise all have decent reviews and I tend to aggregate my information from multiple places and then, if available, try the product’s free trial period first. Anywho…these are some of the top contenders right now, I’ll list them (and no, its not exhaustive), call out some highlights, and then go into what I ultimately chose:
Bark
Qustodio
Canopy
Net Nanny
Aura
Google Family Link
Highlights
Let’s start with Bark, because out of all the choices its the app I would go with. If you want a complete and total monitoring tool, you go with Bark. It’s $99/year, covers multiple devices, and is on top of it with alerts. The main thing with Bark, though, is that it monitors the device for “alert” words, phrases, and activities that could indicate a deeper problem and sends notifications to the parent(s) for further investigation. You don’t get a line-by-line listing of your child’s texts or calls so it allows some freedom and responsibility while also acting as that safety net.
The other apps listed are similar in function, and all offer some ability to restrict activities and apps. Much of the difference, though, is that most of the other apps don’t monitor texts and calls. That being said, I tried a few that had free trials, and I still found Bark to be the most friendly to use and, frankly, its been recommended by several parents and law enforcement officers. Again, the only issue is you have to “side-load” the app.
Our Approach
Okay, so our approach won’t be your approach. But my goal is to start the thinking process and maybe inspire some ideas that you may decide are worth a try. My kids are 9 and I’m a nerd that right now is looking for total control since they simply are not emotionally developed enough to handle social media. That being said, I also recognize that I need them to be comfortable with technology, since it’s not going away, and learn how to cope appropriately since it seems like the schools have them doing most of their work online. I’ve been in the school, I’ve been on the school network. It’s not as secure as it should be.
Locking down the phone
First up is the phone. We’re going with Android since they had a Google account already to use the Chromebooks. FYI…you can set up a Google account for minors, and as the parent through Family Link you can monitor their activity across multiple devices. You can’t however, access and read emails, and unlike Bark, Family Link does not scan their messages, calls, or emails for malicious (or potentially malicious content).

That being said, during phone setup you will be prompted to choose what apps to allow and to block, and its pretty robust. From the parent dashboard you have even more control. Because, right now anyway, our kids really have no need to do anything with a phone other than call us, everything but a handful of apps are blocked. We are actually using this in conjunction with Microsoft Family Safety:
A more complete and effective screening algorithm for web browsing, does a better job at filtering out inappropriate sites and search results on the Edge browser
Grants visibility to sites visited and search activity (unlike Family Link)
Can require parental consent for all websites, or add a list of approved sites
Robust app controls across any Android device with family link installed
Screen time limits and app limits
Geofencing
Can remove, or simply restrict Play Store access and downloads
A little difference that applies to our scenario is that I run a private chat and email server out of my NAS. Because of that, I have visibility to all incoming and outgoing emails from any family member as well as any text messages that go through the chat server. So…we actually disabled all apps other than the mail app for my mail server, our chat app, the Edge browser, Plex (again, our personal media server), and our personal location server. My kids are 9…I’m going to be picky about what they are exposed to right now. I’m not currently using anything but Google Family Link and MS Family Safety, since Bark right now is overkill.
That being said, in a few years when they are more social and have a little more emotional development, Bark may be necessary because at the end of the day they need some freedom. But, this is a start and between the two platforms (plus what we teach them at home), I’m comfortable with the control. Likewise, even at 9 they have a family contract, they know that at home the phone they share is with us and not needed. That may change in a few years, but for now the contract is they give up the phone when they hit the door.
Apps That Should Always be Blocked
The following are apps that should always be blocked. I actually have most of these blocked on my home network in addition to blocked on the phone.
Potentially Inappropriate Apps
| Snapchat | App is GPS-enabled, so pictures may have locations embedded. Likewise, when sending inappropriate images ("nudes"), these never truly disappear |
| Also has "disappearing" messages. Also has a large amount of inappropriate content that is not filtered. | |
| Discord | Large gaming chat rooms that can expose kids to hate speech, bullying, online predators, and can be jumping-off point to other apps with images |
| Yik Yak | Messaging app that allows completely anonymous content to be posted; anyone within a 5 mile radius of a public post can read it (whether its true or not) |
| TikTok | No filters, lots of inappropriate content, and viral trends that have been shown to put children in danger |
| Twitter/X | While the recent change in ownership has been positive for content filtering, there is still a lot of inappropriate content that should be monitored |
| Hoop | This app allows children to connect with strangers (a comparison has been made that this is Tinder + Snapchat). Enough said. |
| Kik | One of the most utilized apps by child predators |
| Vault apps | A generic term for any app that "hides" files and photos. Generally, its a red flag that something is being hidden on the device. |
| Roblox | While the game itself is just a game, the chat is the problem. Exposure to bullying, hate speech, sexual content, and drugs have been noted frequently. |
| Yarn | A reading app that tells stories via fake text messages, this apps stories are usually scary or sexual in nature. |
| YouTube | While this may be surprising, the safe search filters and content filtering for YouTube is not as robust as it should (or could) be |
| Tumblr | |
| Litterally anyone can open a chat room for any discussion; often used as a jumping off point to other apps that are considered less risky for prosecution or being caught. | |
| Most live streaming apps (Twitch, Yubo, Marco Polo, etc.) | Many of these apps share locations, and livestreams can allow kids to access content that was otherwise blocked. |
| Dating apps | Just about all dating apps are simply places for predators and have no place on a child's phone. |
And the end...
This is going to be a “living” post. Updates will ensue. Because tech always changes. I encourage our techy family members to add in the comments. We can all learn and the learning never stops.

About
Nothing in this post is meant to serve as advice or guidance. It’s simply my experience over the last 10 years of researching web content hardening and home network hardening, as well as simply helping others work out of account hacks and issues.


